Groups
CONFIGURE > USER MANAGEMENT > Groups
Groups are used to grant privileges to users. When a user is a member of a group, defined privileges may be granted to the group by an administrator. When editing a group, the (authorised) user selects from a list of devices, all of which are under the heading SERIALLY CONNECTED DEVICES.
Permission Changes in the Web UI
A new feature change called Access Rights is introduced in release 22.11 replaces the previous concept of a user Role and instead uses a set of configurable Access Rights for each group. Each access right governs access to a particular feature (or set of highly related features), with a user only having access to features for which they have an assigned access right.
Tip: To support the new permissions model several rest API endpoints have been updated for the new functionality. Wherever possible, these changes backwards compatible. See the release noted for details.
Understanding Access Rights
An access right is a permit authorizing access to a feature or collection of related features. Holders of the permit (i.e. the access right) are given access to the feature.
A user gains access rights by the following:
-
Access Rights are assigned to Groups.
-
Users are members of zero or more Groups.
-
A User inherits all Access Rights from all the Groups they are a member of.
Some features may require the user to hold multiple access rights to access the feature through a specific interface. For example, a user needs the “right to use the web UI” and the “right to configure serial ports” to make configuration changes to a serial port through the web UI.
DEFINED ACCESS RIGHTS
There are four defined rights (admin, web_ui, pmshell, and port_config) as summarized in the following table.
| Access Rights | Description |
|---|---|
| admin | The admin access right grants a holder access to everything; every feature and every user interface. |
| web_ui |
Permits access for an authenticated user to basic status information via the web interface and rest API. Users can:
|
| pmshell
Restricted CLI |
Permits access to devices connected to serial ports. Does not give permission to configure all serial ports, only to those that are added to the same group containing the pmshell rights. |
| Port Config | Permits access to configure serial ports. This access right gives the holder the ability to configure serial ports. This right does not give the holder the ability to access the serial port. |
Tip: A right may be combined with another right for a feature to be accessible by a user. For example, web_ui to login and port_config to configure a serial port. The port_config right by itself is not useful.
Admin Access Right (admin)
Any user who was previously an Administrator role now inherits the admin access right, giving that user the same “can do everything” permission.
Tip: The Admin Access toggle switch in the Web UI hides other rights selections as Admin Access overrides all other rights.
Web UI Access Right (web_ui)
Any user who was previously a Console User role now inherits the web_ui and pmshell access rights and there are no functional changes for this user.
Tip: From release 22.11 in the Web UI, the Rights checkbox replaces the Roles drop-down selection.
The web_ui access right grants the user the ability to
-
log into the Web UI,
-
see a listing of serial ports (The “Access → Serial Ports” menu item) and to
-
edit a restricted set of user configuration such as changing their own password.
Portmanager Shell Access Right (pmshell)
Any user who was previously a Console User role now inherits the pmshell access rights and there are no functional changes for this user.
The pmshell access right grants the user access to the serial port web terminals and the ability to use pmshell over SSH. These rights are applied only to the access ports to which they have been granted rights.
Port Configuration Access Right
The port_config access right grants the holder of this right the ability to make configuration changes to the serial ports they have been assigned. Note that a user without the web_ui right cannot login to the web UI to configure serial ports, so a user must inherit the web_ui from at least one group.
Access > Serial Ports View
Users with the port_config access right to some serial ports are able to see the Edit link on the Access > Serial Ports page for those ports only. Non-admin users with the port_config role are able to see any active sessions on a port, but are not able to terminate the session.
Configure > Serial Ports View
The Configure Serial Ports page is accessible to users with the port_config and web_ui access rights appear in the navigation sidebar menu. This page lists ports that the user has both port_config and web_ui access rights.
Tip: It is possible to edit all details on these ports, however, changing the “mode” of a port will disconnect any sessions.
Non-Admin Users
Non-admin users with port_config access right are able to perform Serial Port Autodiscovery on the ports that they are able to configure. If autodiscovery is already running, they will be able to see the banner but will not be able to view the autodiscovery logs or cancel the running job. Non-admin users are not able to configure the Serial Port Autodiscovery Schedule and the icon is hidden, but are able to see which ports are configured of the ports to which they have access.
Protected Groups and Users
Certain types of groups and users have protected status, meaning that they cannot be changed or deleted. Protected groups comprise the following:
root - The root user is hard-coded member of the admin group. As such, the root user cannot be deleted.
admin - The admin group cannot be disabled or changed to a non-admin group.
netgrp - The special ‘netgrp’ also cannot be deleted. This group is assigned to users from AAA auth that don’t have a group assigned from the authentication server.
Tip: For these protected groups no 'Delete' button appears beside them in the Web UI.
Understanding Serial Port Access
Serial ports are assigned to a group in the same way as access rights are assigned to a group, however, it is the access rights that are assigned to the same group that determine what a user can actually do with those serial ports. The access rights assigned to one group will only apply to the serial ports assigned to that same group, they do not apply to the serial ports of another group.
For example, a user in a group with port_config and port-01 can configure that port but not access the device (as that requires pmshell access rights).
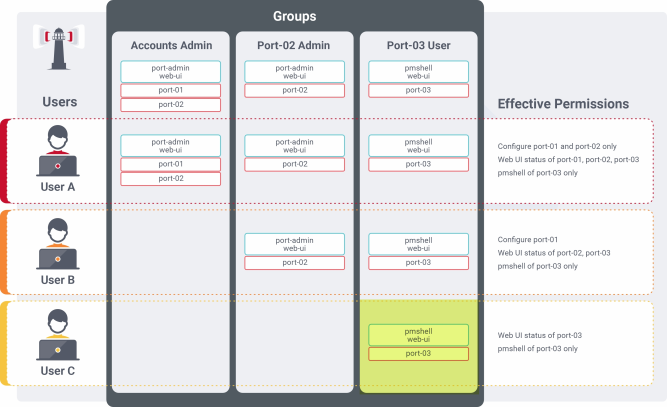
Consider the following two groups, Accounts Admin and Port #03 User:
| Group Name | Accounts Admin | Port #03 User |
|---|---|---|
| Access Rights |
|
|
| Serial Ports |
|
port-03
|
The effective rights for a user in one or both of those groups is shown in the following table. It shows how access rights assigned to one group will only apply to the serial ports assigned to that same group:
The following table shows the effective rights for a user in one or both of those groups, Accounts Admin and Port #03 User:
|
Accounts Admin | Port #03 User | Accounts Admin & Port #03 User | ||
|---|---|---|---|---|---|
Configure port-01 |

|

|

|
||
Configure port-02 |

|

|

|
||
Configure port-03 |

|

|

|
||
Access port-01 |

|

|

|
||
Access port-02 |

|

|

|
||
Access port-03 |

|

|

|
Note:Note the highlighted cell; a user with pmshell access to port-03 (from the Port #03 user group) does not also get port_config for that port, even though that access right is inherited from the Accounts Admin group. The access rights of a group only apply to the serial ports in that same group. This principle is illustrated in the following figure:
The figure below shows how access rights assigned to one group only apply to the serial ports assigned to that same group.
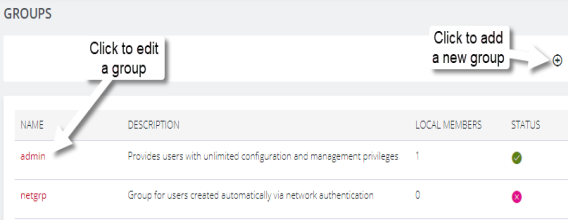
Create a New Group
-
Select CONFIGURE > USER MANAGEMENT > Groups.

|
Add a new group. |
| admin | Click on the group name to edit an existing group. |
|
In the EDIT GROUP window - Enable/Disable an existing group. |
|
Grant admin access rights and full control of this console, and all attached devices, to all users of this group. |

|
Delete a group (or delete selected groups). |
-
Click the Add New Group button. The CREATE GROUP page opens.
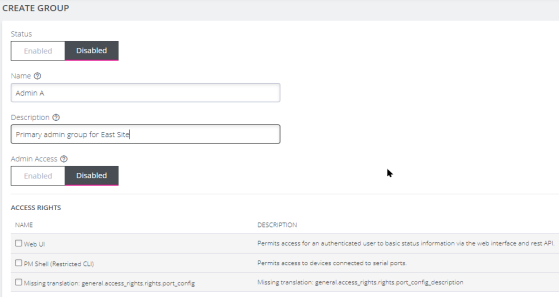
-
Enter a Group Name, Description, and set Admin Access to Enabled or Disabled. Specific access rights can be selected in the ACCESS RIGHTS area.
Note:Group Name is case sensitive. It can contain numbers and some alphanumeric characters. When using remote authentication, characters from a user's remote groups that are not allowed are converted to underscores during authentication. Local groups can be created that take that into account, allowing the authentication to continue.
Note:If Admin Acess is Enabled, members of the group will have full access to and control of selected managed devices, and the rights that are selected under ACCESS RIGHTS for that group.
-
Select the applicable Access Rights for the group (see the below table).
-
If the new group is to be activated immediately, set the group Status to Enabled.
-
Click the Submit button to save the group. After creation, group Status and Admin Access may be enabled or disabled from the CONFIGURE > USER MANAGEMENT > Groups > EDIT GROUP page.
Edit an Existing Group
-
Select CONFIGURE > USER MANAGEMENT > Groups.
-
Click on the name of the group to be modified and make desired changes.
-
Click Submit to save the changes
The CONFIGURE > User Management > Groups page also allows administrators to delete a group. Users who were members of the deleted group lose any access and administrative rights inherited from the group.
Note:The netgrp group is inherited as the primary group for all remote AAA users who are not defined locally. By default, netgrp has the Administrator role and is disabled. It must be enabled to take effect for remote AAA users.
Note:For users that don’t have any group, they are still part of netgrp, even if the netgrp membership is not explicitly enabled for the user.
The permissions for the netgrp members is a union of the permissions that have been given in the netgrp AND the permission for the user in AAA (TACACS+, RADIUS, etc).
If your netgrp “role” says “Console User” and you have priv-lvl 13 in TACACS+ (level 15 being the highest), then the union of that is like an admin already, so setting “console user” in netgrp does not matter.