Brute Force Protection
CONFIGURE > SERVICES > Brute Force Protection
A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until the one correct combination that works.
Brute Force Protection offers an essential defense mechanism by automatically blocking access from offending source IP addresses.
Caution: Brute Force Protection may prevent access to the system during an emergency.
Configure Brute Force Protection
Note:Brute Force Protection is enabled by default for SSH and Web UI.
To configure Brute Force Protection:
-
Navigate to CONFIGURE > SERVICES > Brute Force Protection.
-
Choose the desired settings as described below.
-
Click Apply to save the changes.
| Field | Values | Description |
|---|---|---|
|
SSH Protection |
Enabled / Disabled |
Enable Brute Force Protection for SSH login attempts. |
|
HTTPS Protection |
Enabled / Disabled |
Enable Brute Force Protection for Web UI login attempts. |
|
Maximum failed attempts |
Attempts: 3 (minimum) Time period in minutes: 1 (minimum) |
The number of failed access attempts permitted within the given time period before preventing access. |
|
Lockout period |
60 (minimum) |
The number of seconds that an IP address will be banned after violating the Brute Force Protection policies. |
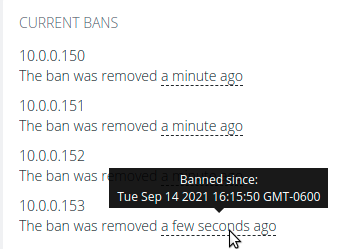
Viewing Current Bans
IP addresses that are currently blocked appear in the CURRENT BANS section of the Web UI, displaying the address and remaining duration of the ban or how long ago the ban was lifted.
Hover over the ban time for more detailed information.
Managing Brute Force Protection via Command Line
For more control over Brute Force Protection, administrative users can use the command line to configure the service and remove bans manually.
| Description | Command |
Notes |
|---|---|---|
|
Display Brute Force Protection configuration |
ogcli get services/brute_force_protection |
|
|
Update Brute Force Protection configuration |
ogcli replace services/brute_force_protection << END |
Ban time in seconds. Find time in minutes. |
|
Un-ban an IP address |
fail2ban-client unban <ipaddress> |
|
|
Un-ban all current bans |
fail2ban-client unban --all |
|
|
List SSH bans |
fail2ban-client status sshd |
SSH protection must be enabled. |
|
List HTTPs bans |
fail2ban-client status https |
HTTPs protection must be enabled. |
|
List all bans with ogcli |
ogcli get monitor/brute_force_protection/bans |
|