Network Access Policies for Operations Manager
In a more complex deployment, Opengear appliances may be connected to multiple networks or virtual networks (VLANs), and in these cases it is often important to be able to control which of these networks each authenticated IP Access user is able to access.
This feature is only supported on Operations Manager or OM Series appliances, which support the zone-based firewall, designed to work with multiple VLANs and the optional built-in Ethernet switch with layer-3 capable ports. This flexibility and control is very useful, especially for customers who have a number of separate management networks (or VLANs) for different administrative teams.
The Network Access Policy mechanism on Lighthouse provides a way to dynamically map IP Access users, based on their group membership, to the firewall zone(s) that they can access on the Nodes. Each firewall zone is a collection of network interfaces which is configured on each Opengear appliance or Node. Firewall zones are used to provide policy abstraction by logical zone names – the physical or virtual interfaces on each Node may vary by site, but the zone names must stay consistent. It is recommended that zones and names are planned out in advance of implementation.
A firewall zone is a collection of network interfaces which is configured on each Opengear appliance or Node in Lighthouse terminology. The Network Access Policy mechanism on Lighthouse provides a way to map users, based on their group membership, to the firewall zone(s) that they can access on the Nodes.
Understanding Access Policies
Putting it all together, when a user authenticates to Lighthouse, they are mapped into one or more group(s), which map into firewall zone(s), which allow authenticated users to reach the appropriate network interfaces(s), including switch ports or VLANs, via IP Access.
For example, users who belong to the security group may get mapped into the secops (security operations) zone. On each OM appliance, the appropriate switch port(s) and/or VLAN(s) for security operations should be configured to be in the secops zone.
Similarly, users in the server group may get mapped into the serverops zone, and again on the OM appliances the appropriate interfaces can be configured to be part of that zone. The result is that members of the security group get IP Access to the networks in the secops zone, and members of the server group get IP Access to the networks in the serverops zone, for each Node that they connect to.
Setting up Network Access Policies
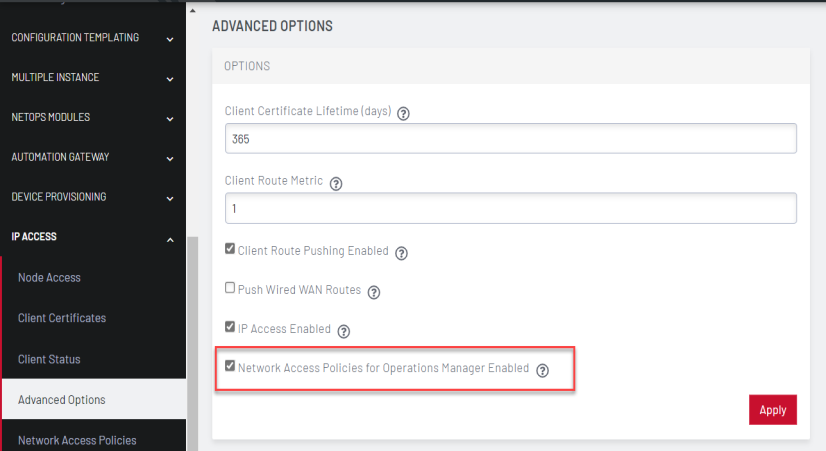
To enable this feature, go to IP Access > Advanced Options and select “Network Access Policies for Operations Manager Enabled”, then hit Apply.
To set Access policies
A policy must be configured for each group whose members will use IP Access.
-
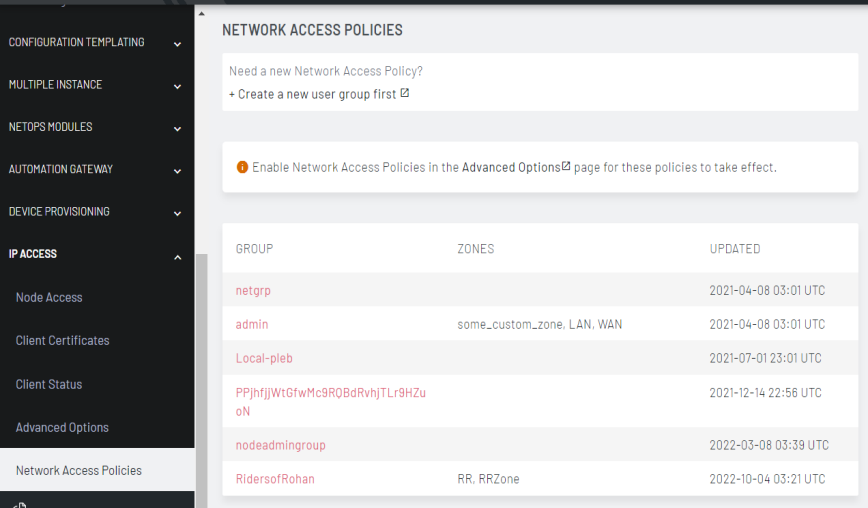
Select Configure > IP Access > Network Access Policies. The Network Access Policies page displays. The group to zone mapping column names ZONES is empty by default.
-
Click on the group name to edit the group policy.
-
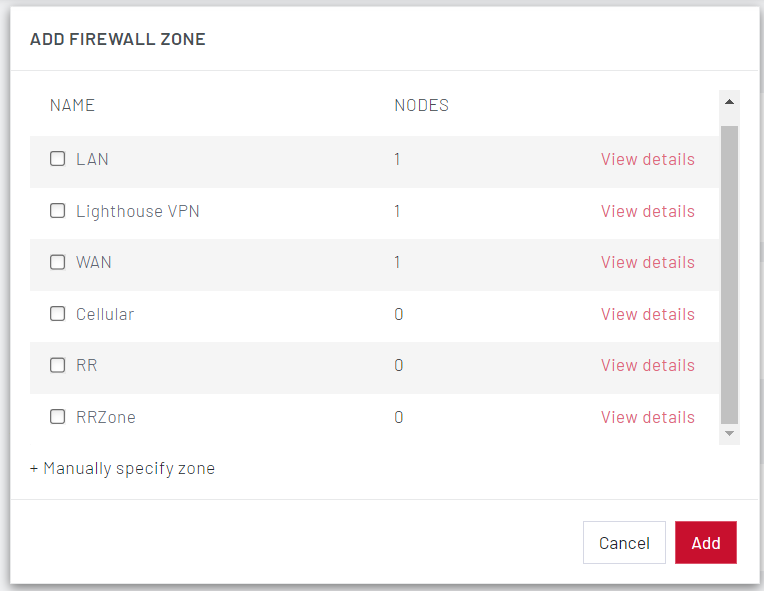
Click on + Add Zone to add one or more firewall zones for this group.
-
Select the firewall zone and click Add.
-
The Network Access Policies page now displays the group with the Firewall zone.