Firewall Management
CONFIGURE > FIREWALL > Management
Navigate to the Firewall Management page, CONFIGURE > FIREWALL > Management, from here you can:
-
Add a new firewall zone.
-
Add a firewall service.
-
Edit a firewall zone - manage the zone setup.
-
Manage port forwarding.
-
Manage custom rules for firewalls.
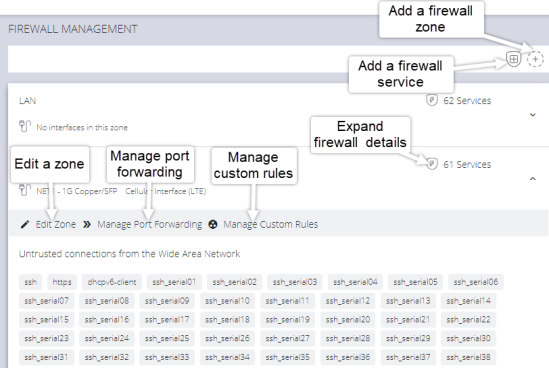
Firewall Management main page
Firewall Zone Settings
To change firewall management settings navigate to CONFIGURE > FIREWALL > Management.
Note:The application of any custom rules will result in Permit All Traffic being enabled in a zone.
You can inspect details of any zone by clicking the Expand icon to the right of the zone. Once expanded, you can click Edit Zone to change settings for a particular zone.
The Edit Zone page has three tabs. The ZONE SETUP page allows you to:
-
Modify the Name of the zone.
-
Add a Description for this zone.
-
Permit all Traffic.
-
Masquerade Traffic.
-
Select Physical Interfaces.
-
Manage Permitted Services by clicking on Plus or Minus next to each.
Tip: You can use the Filter Interfaces and Filter Available Services text boxes to limit the list content that is displayed.
Port Forwarding
The MANAGE PORT FORWARDING tab allows you to add, edit, and delete forwarding rules for the particular zone you are editing.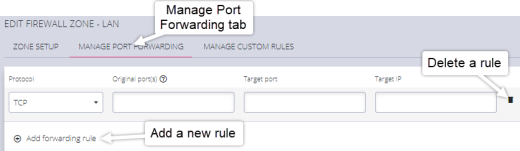
Manage Custom Rules
Note: The application of any custom rules will result in Permit All Traffic being enabled in a zone.
The third tab, MANAGE CUSTOM RULES, allows you to add, edit , and delete custom firewall rules for the zone you are editing. These custom rules continue to exist after reboots, upgrades, and power cycles.
These rules are prioritized by the order they are added.
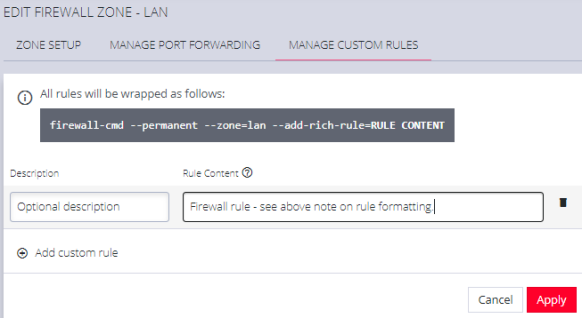
To add a new custom rule:
- Click Add custom rule.
- Enter an optional description for this rule.
- Enter the rule content, custom rule content formatted with firewall-cmd syntax.
- Click Apply.
Note: All rules will be wrapped as follows:
firewall-cmd --permanent --zone=lan --add-rich-rule=RULE CONTENT
Firewall - Source Address Filtering
Source address filtering provides an interface by which users can permit access to services (for example, SSH, HTTPS, SNMP) on a device from specific source addresses.
This feature removes generic or global permitted services within firewall zones, and instead allows users to permit a service on a specified source address (or address range) within the firewall zone. Source address filters configured in a zone apply to all the interfaces within that zone.
To access the feature, navigate to the Configure > Firewall > Management page through the WebUI then select the current source address filter configuration under the services in zone tab for each zone.
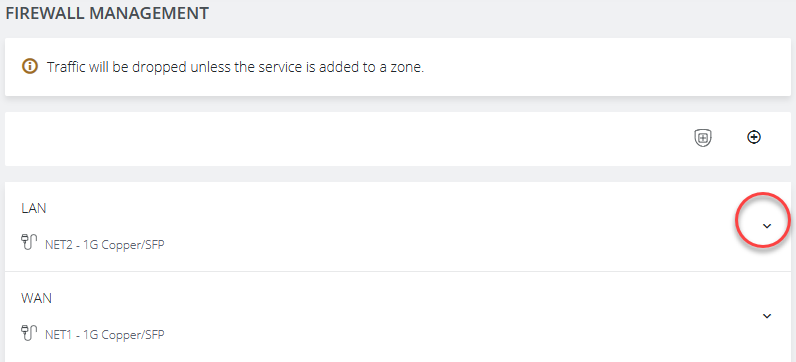
To add a source address filter for a zone, select the edit zone option under the desired zone, which opens the edit zone page where source address filters can be configured.
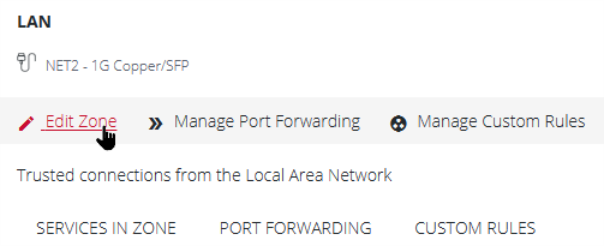
You can choose to enable permit all traffic, which will permit all traffic in the zone
(unless there is a custom rule configured overwriting this behavior).
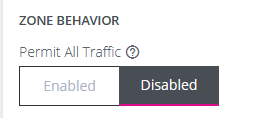
If the permit all traffic option is disabled, you will have the option to configure permitted services for any allowed source address. Permitted services can be added or removed from each source address filter under the "Services" field.
Source address filters can be added, duplicated or deleted by using the buttons below and to the right of the filter. Any new changes to the source address filters can be seen under the services in zone tab for each zone on the main firewall management page.
Firewall Source Address Bulk Services
Configure > FIREWALL > Management > New Firewall Zone
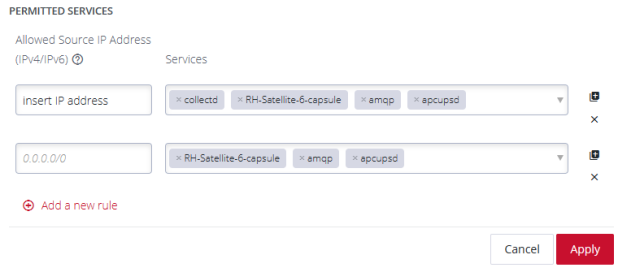
PERMITTED SERVICES
The firewall source ip field allows you to assign permitted services to specified source ip addresses in bulk rather than needing individual rich rules to add each specific service. This change allows you to easily target specific IP Addresses with permitted services. Enter the target IP address, select services from the drop-down list and click Apply.
Firewall Egress Filtering
Firewall egress filtering may be used to allow or deny traffic leaving a device. This feature allows you to create firewall egress rules, which govern outgoing traffic leaving the device.
Firewall egress filtering extends the firewall/policies endpoint, allowing customization over both incoming (ingress) and outgoing (egress) traffic, thus allowing greater control of the device’s security.
The feature allows you to:
-
Change the default behavior of a firewall policy so it can accept or deny traffic moving between zones.
-
Create, edit and delete firewall policy rules which allow or block specific service traffic based on IP addresses.
-
Configure firewall policy rules through ogcli, config shell or the WebUI.
-
Display and inspect rules in a single location in the WebUI.
-
Create symbolic zones HOST and ANY which allow the creation of catch-all firewall policies affecting traffic incoming and outgoing all zones.
CREATING EGRESS POLICIES ON THE WEBUI
Configure > FIREWALL > Policies
New policies or edits of existing policies are done from the Firewall Policies page. Navigate to Configure > Firewall > Policies, there is now an overview for firewall policies created on the device, as well as an overview page showing firewall policy rules created. To view firewall policy rules, click the drop-down arrow to the right of any policy row.
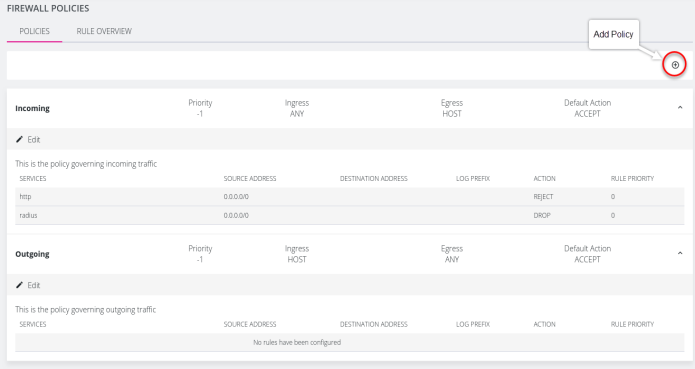
CREATING NEW EGRESS POLICIES
New policies are created by first clicking on the Add Policy button at the top-right of the Firewall Policies page of the WebUI. New policies can have a user-defined default action, either ACCEPT, CONTINUE, DROP, or REJECT, which describes how traffic moving through the ingress and egress zones will be treated. The ingress and egress zones may be configured as custom zones on the device through the firewall/zone endpoint, or can be symbolic (ANY/HOST) which represent traffic on all interfaces and the host device itself respectively. These default actions are described below.
| Default Action | Outcome |
|---|---|
| ACCEPT | All packets flowing between ingress and egress zones are accepted by default. |
| REJECT | Rejects every packet (a message warns that the connection was rejected and that packets will not be allowed through):ssh: connect to host 10.236.3.7 port 22: Connection refused |
| DROP | Drops every packet (users will not get a message, the connection will hang). |
| CONTINUE | Ongoing packets will be subject to rules in following policies and zones. |
CREATE A NEW FIREWALL POLICY
-
Click on the Add Policy button at the top-right of the Firewall Policies page of the WebUI.
-
Complete the Name, Description, Default Action and Policy Priority inputs of the New Policy.
Note: Policy Priority - Policies with negative values are applied before any filtering rules in zones. Policies with positive values are applied after filtering rules in zones. A priority of 0 (zero) cannot be applied.
-
Select the required Ingress and or Egress zones.
-
Click on the Add New Rule button and complete the information; Source and Destination address, also Log Prefix are optional.
-
Click Apply. The new rule is instated.
EDITING POLICIES OR RULES
Rules associated with a policy can be edited. When saving their changes after editing, you are prompted to double check their changes using the Confirm Action window, which presents an overview of the policy changes.
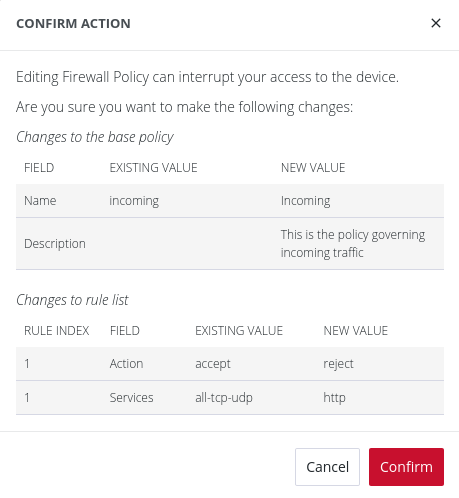
Note: Editing a firewall policy or rule may interrupt access to the device.
CONFIGURE EGRESS POLICIES IN THE CONFIG SHELL
Firewall policies may be created through config shell an example is given below:
config: firewall/policy
config(firewall/policy): add incoming
config(firewall/policy incoming): default_action accept
config(firewall/policy incoming): egress_zones
config(firewall/policy incoming egress_zones): add host
config(firewall/policy incoming egress_zones): up
config(firewall/policy incoming): ingress_zones
config(firewall/policy incoming ingress_zones): add any
config(firewall/policy incoming ingress_zones): up
config(firewall/policy incoming): show
Entity firewall/policy item incoming
default_action accept *
description ""
name incoming
priority -1
egress_zones (array)
0 host *
ingress_zones (array)
0 any *
rules (array)
| Policy Configurable Fields | |
|---|---|
| default_action | The default action that is applied to packets that don't match any rule. |
| priority | The priority of the policy dictates when it is applied compared to other policies and zones. Policies with negative priorities are applied before rules in zones; policies with positive priorities are applied after. A priority of 0 is reserved for Rules and is not used for policies. The default value is -1. |
| egress_zones | Traffic directed to the egress zones will be subject to this policy. This was pre-existing but has been expanded to include options for ANY/HOST. |
| ingress_zones | Traffic originating from the ingress zones will be subject to this policy. This was pre-existing but has been expanded to include options for ANY/HOST. |
| rules | A list of rules that specify what happens to specific packets as they pass through the firewall policy. |
CREATE RULES UNDER A POLICY - CONFIG SHELL
The rules that apply to a firewall policy may be created through Config Shell; an example is given below:
config(firewall/policy incoming): rules
config(firewall/policy incoming rules): add
config(firewall/policy incoming rules 0): show
Entity firewall/policy item incoming field rules 0
action "" (required)
destination_address ""
log_prefix ""
priority 0
source_address ""
services (array)
| Rule Configurable Fields | |
|---|---|
| action | The action that will be applied to matching packets. |
| destination_address | The destination address to which this rule will apply. |
| log_prefix | This sets the prefix of the info level log that is sent when this rule is hit. If it is empty, no logs are sent. |
| priority | The priority given to the selected rule. Rules with negative priorities are applied first. The default value is 0. |
| source_address | The source address to which this rule will apply. For multiple source addresses, a separate rule must be created for each address. |
LOGGING AND DEBUGGING FIREWALL POLICIES
Some logging and debugging tools are provided for resolving firewall policy issues, as below:
-
List all firewall policies configured on the device:
firewall-cmd --list-all-policies. -
Check the xml files which contain the firewall policy configuration information, under the /etc/firewalld/policies/ directory.
-
Check the journal for firewall related messages:
journalctl -xeu firewalld
Note: firewalld is used to create firewall rules, firewalld is discussed in Interzone Policies and in Firewall Guide.